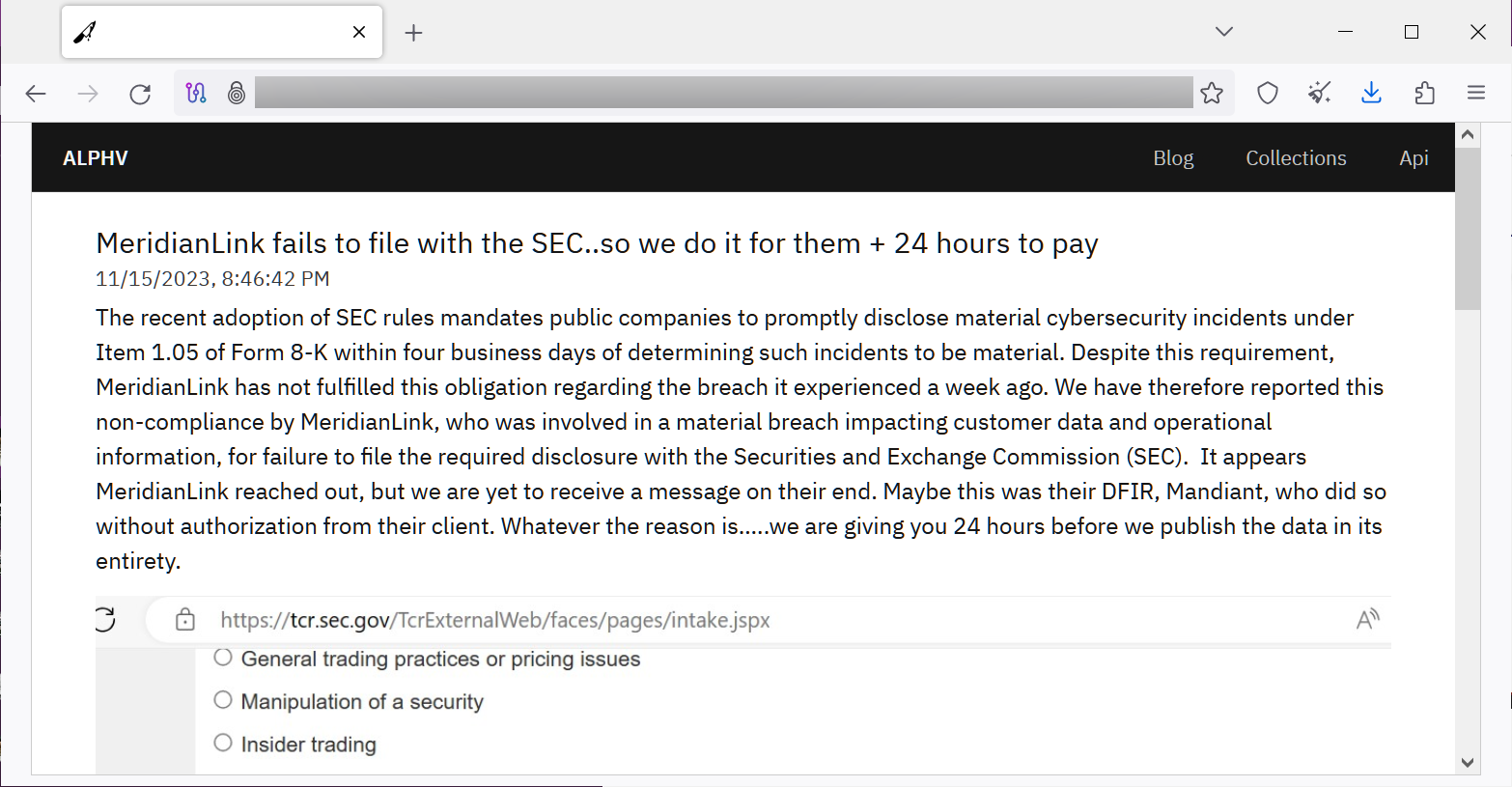
More than 1 million Michiganders affected by Welltok cyberattack
KRISTEN JORDAN SHAMUS Detroit Free Press
13 hours ago
More than 1 million Michiganders were affected by a cybersecurity breach at Welltok Inc., a software company contracted to provide communication services for Corewell Health's southeastern Michigan properties along with a healthy lifestyle portal for Priority Health, an insurance plan owned by Corewell.
For about 2,500 Priority Health members, names, addresses and health insurance identification numbers were compromised, the health plan said in a statement.
For about 1 million Corewell Health patients, the compromised data includes names, dates of birth, email addresses, phone numbers, medical diagnoses, health insurance information and Social Security numbers.
Attack hit nearly 8.5 million people nationally
Welltok, which is owned by Virgin Pulse, sent letters earlier this month to people affected by the massive breach. According to the U.S. Department of Health and Human Services Office for Civil Rights, which publishes a list of all breaches of protected health information that are under investigation involving 500 or more people, the Welltok cyberattack affected 8,493,379 people.
Those affected included people who have received health care or insurance provided by the following companies, according to Welltok:
- Asuris Northwest Health
BridgeSpan Health
Blue Cross and Blue Shield of Minnesota and Blue Plus
Blue Cross and Blue Shield of Alabama
Blue Cross and Blue Shield of Kansas
Blue Cross and Blue Shield of North Carolina
Faith Regional Health Services
Hospital & Medical Foundation of Paris, Inc. dba Horizon Health
Mass General Brigham Health Plan
Regence BlueCross BlueShield of Oregon
Regence BlueShield
Regence BlueCross BlueShield of Utah
Regence Blue Shield of Idaho
St. Bernards Healthcare
Sutter Health
Trane Technologies Company LLC and/or group health plans sponsored by Trane Technologies Company LLC or Trane U.S. Inc.
The group health plans of Stanford Health Care, of Stanford Health Care, Lucile Packard Children’s Hospital Stanford, Stanford Health Care Tri-Valley, Stanford Medicine Partners, and Packard Children’s Health Alliance
The Guthrie Clinic
Breach went undetected for more than two months
In a statement, Welltok said it "takes this incident very seriously" and recommends credit monitoring for those affected by the breach, which occurred May 30 when a cyberattacker exploited software vulnerabilities on the MOVEit Transfer server, which is supposed to provide the secure digital transfer of sensitive information, including protected health information.
Welltok said it had installed all the required MOVEit Transfer security upgrades and patches as soon as they were available and conducted an examination of its networks and systems to identify any potential for compromised data. It wasn't until Aug. 11, after the company hired third-party cybersecurity specialists and reconstructed its systems and historical data, that the breach was discovered.
"While we have no evidence that any of your information has been misused, we are notifying you and providing information and resources to help protect your personal information," Welltok said in a statement.
"The following types of information may have impacted: name and address, telephone number, email address. The type of information at issue varies for each person. For a small group of impacted clients, Social Security numbers, Medicare/Medicaid ID numbers, or certain health insurance information such as plan or group name, were also implicated. For other individuals, certain health information such as a provider name, prescription name, or treatment code may have been included."
Welltok opened a dedicated assistance line at 800-628-2141 to help address any questions people may have.
Cybersecurity attacks are a growing problem in health care
The HIPAA Journal reported that the cyberattack at Welltok is the fourth-largest health care data breach in the U.S. this year. The U.S. Department of Health and Human Services reported that data breaches among health care organizations more than doubled from 2019 to 2021. And in 2022, at least 28.5 million health care records were breached.
In Michigan alone, several have been reported in recent months, including one that affected 2.5 million patients of McLaren Health Care.
A ransomware attack took down the computer network at McLaren's 14 Michigan hospitals in late August and early September. The health system acknowledged in October that it also could have leaked some patient data onto the dark web. A ransomware gang known as BlackCat/AlphV claimed responsibility for the cyberattack, posting online that it stole 6 terabytes of McLaren's data.
And in late August, the University of Michigan shut down its campus computer network after a hacker got access to the personal information of students and applicants, alumni and donors, employees and contractors, as well as the personal health information of research study participants, and patients of the University Health Service and the School of Dentistry.
The data that was compromised in the U-M cyberattack varied, but for some included Social Security numbers, driver’s license or other government-issued ID numbers, financial account and payment card numbers. For others, it also included medical record numbers, diagnoses, treatment or medication history, and other clinical information.
https://eu.freep.com/story/news/health/ ... 735567007/